view the rest of the comments
Lemmy Shitpost
Welcome to Lemmy Shitpost. Here you can shitpost to your hearts content.
Anything and everything goes. Memes, Jokes, Vents and Banter. Though we still have to comply with lemmy.world instance rules. So behave!
Rules:
1. Be Respectful
Refrain from using harmful language pertaining to a protected characteristic: e.g. race, gender, sexuality, disability or religion.
Refrain from being argumentative when responding or commenting to posts/replies. Personal attacks are not welcome here.
...
2. No Illegal Content
Content that violates the law. Any post/comment found to be in breach of common law will be removed and given to the authorities if required.
That means:
-No promoting violence/threats against any individuals
-No CSA content or Revenge Porn
-No sharing private/personal information (Doxxing)
...
3. No Spam
Posting the same post, no matter the intent is against the rules.
-If you have posted content, please refrain from re-posting said content within this community.
-Do not spam posts with intent to harass, annoy, bully, advertise, scam or harm this community.
-No posting Scams/Advertisements/Phishing Links/IP Grabbers
-No Bots, Bots will be banned from the community.
...
4. No Porn/Explicit
Content
-Do not post explicit content. Lemmy.World is not the instance for NSFW content.
-Do not post Gore or Shock Content.
...
5. No Enciting Harassment,
Brigading, Doxxing or Witch Hunts
-Do not Brigade other Communities
-No calls to action against other communities/users within Lemmy or outside of Lemmy.
-No Witch Hunts against users/communities.
-No content that harasses members within or outside of the community.
...
6. NSFW should be behind NSFW tags.
-Content that is NSFW should be behind NSFW tags.
-Content that might be distressing should be kept behind NSFW tags.
...
If you see content that is a breach of the rules, please flag and report the comment and a moderator will take action where they can.
Also check out:
Partnered Communities:
1.Memes
10.LinuxMemes (Linux themed memes)
Reach out to
All communities included on the sidebar are to be made in compliance with the instance rules. Striker
So data stores tend to present interfaces which allow the CRUD operations on each record: Create, Read, Update, and Destroy.
Create: You hit submit on a comment form Read: Your client app shows the content of the comment Update: You hit submit on the comment editing form Destroy: You delete the comment
Well, in some cases it’s very handy to make a data store with only two operations: Create, and Read.
This is called a “log”. A log is an append-only data structure.
One of the benefits of using a log is that two different processes can operate on the data, at different times, and can be confident they’re operating on the same context despite not being in communication with each other.
This “log” structure could be useful for instance in recording the moves of a chess game. Then, a hundred years later, someone can read each move out of a book and deterministically re-create the board state.
Now they know that they are looking at the same chess game that Ben Franklin was in 1775, despite not being in touch with Ben at all.
Really big, distributed systems benefit from this “synchronization without communication” feature of logs.
Excellent article on this data structure and its benefits here: https://engineering.linkedin.com/distributed-systems/log-what-every-software-engineer-should-know-about-real-time-datas-unifying
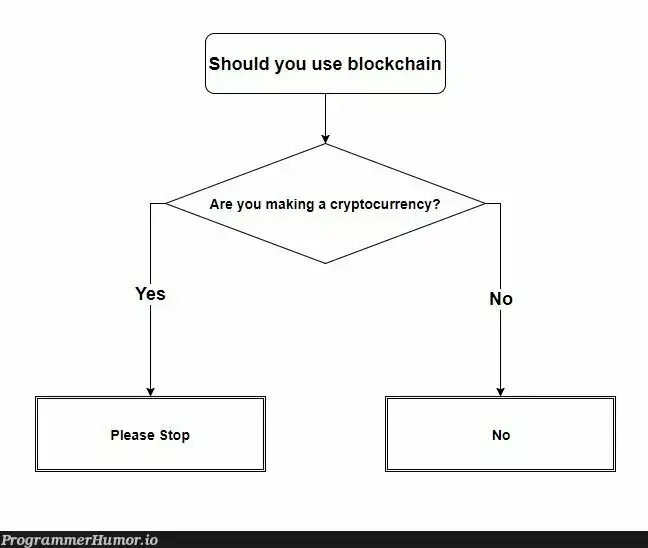
Blockchain is a log.
Relying on a log requires you to trust that nobody else has Update or Destroy access. For it to work correctly and everyone be on the same page, Updates and Destroys need to never happen.
With a coordinated system like people trying to understand historical chess games, or a corporation like LinkedIn seeking its own self interest, there’s no trust issue.
But with other things, like “who’s got how much money”, people don’t want to have to trust that some centralized log owner is modifying the data on the sly.
That’s where blockchain goes beyond a regular log. It’s a log designed to resist tampering, because each “block” in the chain goes through a distributed checking process where many copies of the log are used, and everyone checks each other’s copies to ensure nobody is cheating.