Wait: Are we sure they're actually people?
riskable
"Ma!"
Also, it has to be shouted. As a kid—coming into the house from who-knows-what adventure where I destroyed an item of clothing—again. Or as an adult trying to reach her over the sound of Fox News with the volume up way too loud.
This is the way.
"It's the work of the devil!"
Maybe they were right all along. 🤔
From the article it looks like generative image AI is mainly replacing stock photography more than anything else.
Even if you use AI to make a logo you'll still want a graphic designer to tweak it. So ultimately it really just saves the designer a bit of time.
ACK!
No cap: Whoever said that is goating with the sauce!
Nah, screw that! There's hot singles in your area and doctors hate this one trick. You'll never guess what happens after we nurse this injured kitten (that we injured ourselves) back to health!
To learn more about that thing you searched for you'll find more information before talking about that thing you searched for. It's a totally common thing to search all about. Many people will search for that thing and a common way to solve it is to search for that thing and read the instructions below.
Republicans: Sounds good 👍
Trust me when I say that if you do this with that many girls in the bed... Urine trouble!
It's just a clever way of saying she's psycho 👍
Get a tortoise and feed the berries to it 👍
(That's what we do at our house)




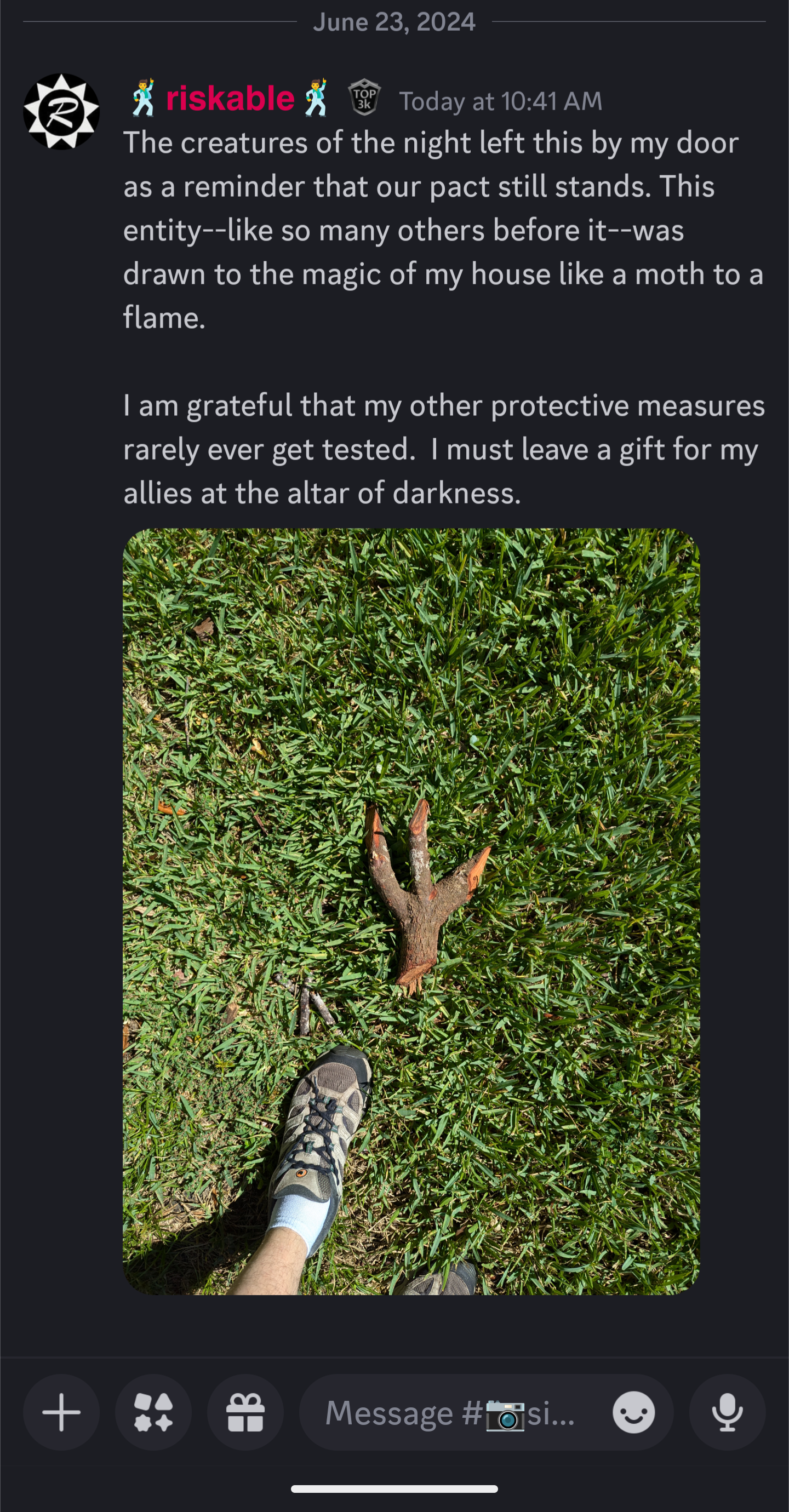
Microsoft is trying to make Xbox into Windows: Where 3rd parties make the hardware and then license the platform from Microsoft. It's a vastly more profitable model. Especially if they get all those end users signed up for a subscription service.
The problem is that the world thinks of "Xbox" as a console (and a specific kind of controller). To pull this off Microsoft is going to have to re-brand Xbox entirely by making people think of it more like a game-specific app store that runs on Windows and special handheld hardware. It won't be easy.
There's a bigger problem with this plan though: No real coordination with the Windows OS team. Windows on handhelds sucks. The past twenty fucking years of Windows development has been almost entirely focused on improving enterprise features with very little attention paid to end users or gaming.
Growth in Windows gaming has come despite Microsoft's investments. Not because of them. In fact, I'd argue that if it weren't for Steam, Windows—as a gaming platform—would be a fraction of what it is today.
Don't get me wrong, though! I love this new Xbox roadmap! Windows gaming has been holding back Linux desktop adoption for far too long. The latest benchmarks that show games on SteamOS vastly outperforming the new Xbox-branded handhelds pretty clearly demonstrates all that bashing of Windows by Linux nerds was deeply accurate.
It turns out that Linux on the desktop really is superior! 🤣